One of the major movie studios is facing a hack attack. Sony Pictures’ computers have been rendered inactive by a hacker group which calls itself Guardians of Peace (#GOP). The group took control of some official twitter accounts and was tweeting the same message across all accounts.
Sony Pictures sits at the top brass of movie production studios in Hollywood. It has produced blockbuster franchises such as Spider-Man, Men in Black, Underworld, and Resident Evil. The hackers have captured the computers of Sony Pictures across the country with an image of CGI skeleton. This image warned that if GOP’s demands aren’t met then they will release sensitive information (that they have stolen from Sony’s repository) to the world at 6 p.m. Eastern Time today. Demands of GOP are unsure as of now.
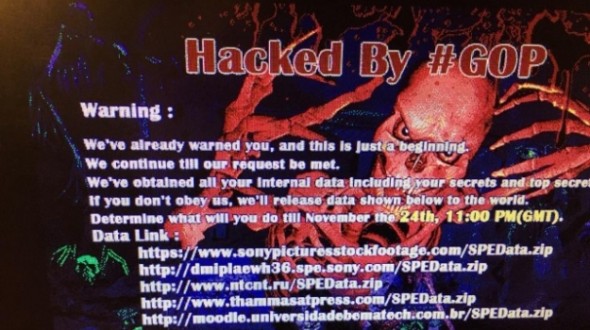
The group has posted .zip files that contain the details of data that they have stolen. These include sensitive data such as financial documents and a lot of passwords. Reddit users are already working on uncovering the .zip files, and it does have a list of important documents including passport information of major stars. Looking at the severity of this hack, the employees were told to shut off their system and go home. Sony Pictures have just said that they are investigating the ‘IT matter’.
Activism is an important aspect of society; it keeps the people in power under check. Hacktivists group like Anonymous constantly target websites and cyberinfrastructure to send out a message, but they do it ethically and don’t cause severe damage to the institutions they target. But this hack by GOP amounts to theft and blackmailing and can cause major harm to the company. Actions like this brings down the value of activism and changes perception of hackers in the eyes of the general public as high tech but lowly thieves. We still have to wait and see how this stand-off ends, but one thing is sure that this is a deplorable act by this hacking group.