If you are an iPhone user, you must be used to the random popup asking for your Apple ID and password because of some app running in the background. It is as normal as it gets and we barely think twice before entering the password. However, there is a new phishing attack which can trick you into giving up your password and cause serious privacy concerns.
A blog post from developer Felix Krause explains how a fake popup could be easily used to trick someone into handing over their Apple ID and password. The developer explains that creating a fake popup doesn’t require extraordinary coding skills. Any iOS engineer can make the Apple ID password prompt and send that popup. The password can then be logged in the app for anyone to access it. It takes less than 30 lines of code and could seemingly be dropped in any legitimate iOS app and sneak past App Store review teams.
Showing a dialog that looks just like a system popup is super easy, there is no magic or secret code involved, it’s literally the examples provided in the Apple docs, with a custom text. I decided not to open source the actual popup code, however, note that it’s less than 30 lines of code and every iOS engineer will be able to quickly build their own phishing code.
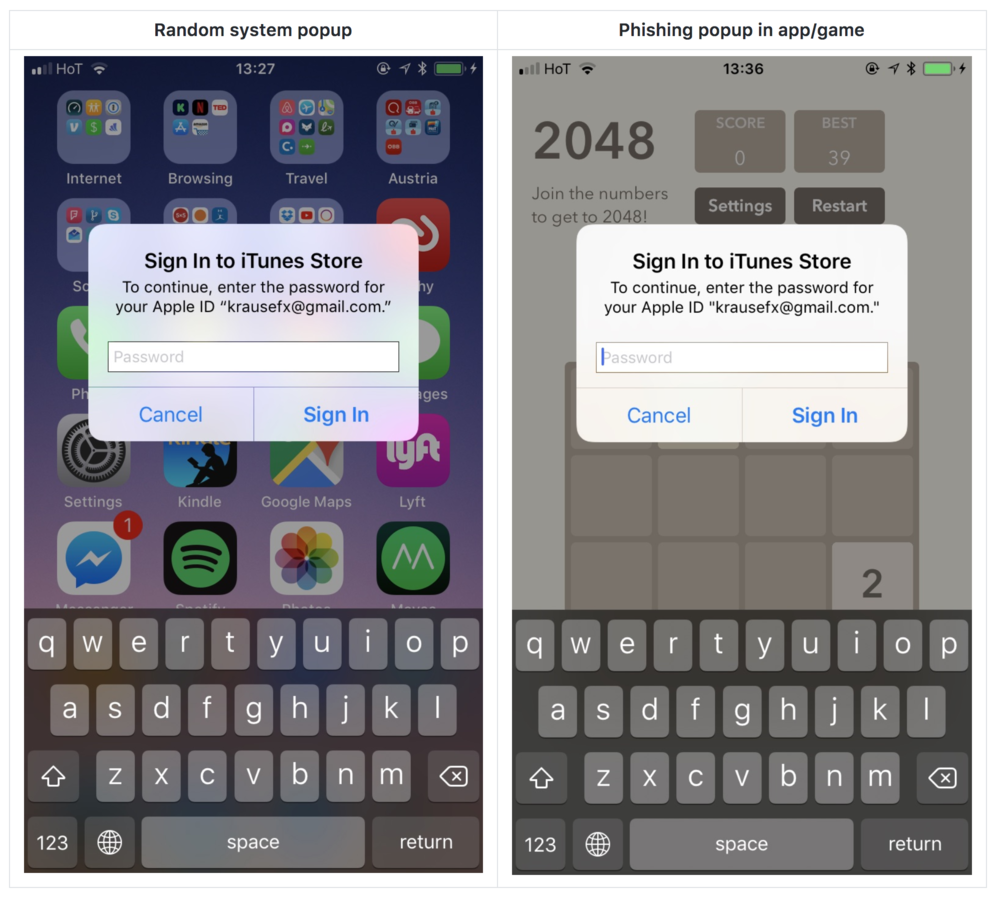
He says he’s already filed this issue as a radar with Apple and explains that it could be fixed by Apple not allowing passwords to be entered in popups, but rather only in the Settings app/App Store. He notes in his blogs that this has been an issue with desktop browsers for years, with websites sending popups which look identical to the system popups.
This seems like a serious issue and until Apple comes up with a solution, Krause has pointed out a few ways you can protect yourself from this phishing attack:
Hit the home button, and see if the app quits:
- If it closes the app, and with it the dialog, then this was a phishing attack
- If the dialog and the app are still visible, then it’s a system dialog. The reason for that is that the system dialogs run on a different process, and not as part of any iOS app.
- Don’t enter your credentials into a popup, instead, dismiss it, and open the Settings app manually. This is the same concept, like you should never click on links on emails, but instead open the website manually
- If you hit the Cancel button on a dialog, the app still gets access to the content of the password field. Even after entering the first characters, the app probably already has your password.