A 15-year-old UG Nazi hacker going by the name of Cosmo or Cosmo the God was sentenced in juvenile court on Wednesday with terms for six years without any computers or Internet, until his 21st birthday.
Tag: hacker
-
15 Year Old Hacker ‘Cosmo The God’ Banned From Internet For 6 Years
During these 6 years, he’ll need approval from his parole officer to access the internet. Wired report that hacker resides in Long Beach, California, and began as a politicized group that opposed SOPA, took down a bevy of websites this year, including those for NASDAQ, CIA.gov, and UFC.com. It redirected 4Chan’s DNS to point to its own Twitter feed.Hacker pled guilty to more than a few felonies, with charges ranging from credit card fraud to online impersonation. The probation that Cosmo agreed to as part of his plea limits his use of the internet to solely educational purposes, and all use will be supervised.As part of the hacker group UGNazi, he was able to gain access to accounts on sites including Amazon, PayPal, Microsoft, Netflix, and many more.He is prohibited from having contact with any members or associates of UG Nazi or Anonymous, along with a specified list of other individuals. Also, according to Cosmo, violating any of these terms will result in a three-year prison term.[The Hacker News] -

Domino’s India Website Hacked, Data Leaked
A Turkish hacker’s group called ‘Turkish Ajan Hacker Group’ has hacked the Indian website of leading pizza company Domino’s. The company’s India operations is handled by its franchise Jubilant FoodWorks. The news was first reported by Cyberwarnews.
Post hacking the site, the Group leaked details of around 37,000 accounts on Pastebin.com. These included names, contact details (phone numbers, email id’s, city details) as well as passwords. According to Business Standard, the hackers used the SQL injection method and remote file inclusion for getting the data.
However, the website is still operational and is still allowing users to place orders.
-
iOS 5.1 gets untethered Jailbreak, even on the new iPad – Release Unknown
iOS Hacker pod2g has released a video of an untethered jailbreak for all Apple iOS devices including the new iPad. The video shows a jailbroken iPad 3 that manages to stay that way even after a reboot. pod2g has yet to announce a public release of this crack, or even if he intends to. Check out the video, but don’t hold your breath for too long.
-
Siri Fully ported and running on iPhone 4 and iPod Touch 4th gen yet with no future
Troughton-Smith has been able to successfully port Siri to the iPhone 4 along with a full connection to Apple Servers. The video below not only shows the Siri functionality on an iPhone 4, but is in depth and shows a side-to-side comparison against its newer, faster sibling, the iPhone 4S. The port proves that the software can easily be enabled on the older device and hence points a finger at Apple for not doing so.
Smith did use a jailbroken iPhone 4s to port the necessary files to the older iPhone 4 which was also jailbroken. When asked if he would seed Siri as a package on Cydia he replied
No, I could not be a part of that. I have no doubts that others will package this up and distribute it quasi-illegally, or try and sell it to people. I am only interested in the technology and making it work; proving that it works and works well on the iPhone 4 and other devices.
So despite the fact it can be done, Smith will not be the one to enable it on your device. Apple has to man up to the truth and enable it for the users, until some Jailbreak dev who is not afraid of Apple Law-Suits does it anyway.
-
Team-Touchdroid dual boots Android on TouchPad
While we still un-package our touch pads, Team Touchdroid has managed to dual boot WebOS and Android 2.3 on he Touchpad. Since the Fire sale, touch pads are all over the place and everyones got in on the action. Especially folks trying to boot Cyanogen Mod 7 on the Touchpads. But looks like its going to be stock droid for now.
For the time being the touchscreen is not working, but expect a quick fix. If you managed to score a Touchpad this might interest you.
-
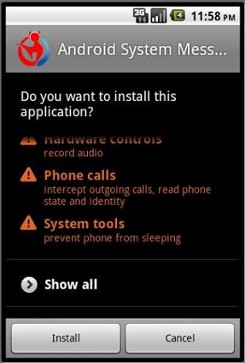
Have an Android Phone, this Trojan will record your Phone Calls!
Are you somebody important, do you work in a big corporation, or even for the government? Do you have an Android Phone? You might consider changing devices after reading this article. A new trojan app / bot that installs itself on any Android device via piggybacking over unknown source apps has found its way into the Android architecture. Ca Technologies found that this easily built app lookalike trojan records your conversations and installs like any other app.
There is no solid information weather this trojan has been released into the world, or if devices are already prey to such a menace. It goes to say some developer could easily capture your calls and upload them to a remote server. The brilliant part about it is that while installing you might get a warning stating that the app will record your calls, but who reads the terms page anyway?
Next time you are installing an App on your Android device , especially via an unknown source, or patched apps, make sure you go through the permissions page with vigilance.
-
Apple iOS 4.3.4 will Fix the Jailbreak and Security Flaws.
 [dropcap]T[/dropcap]he PDF exploit that was used in JailreakMe last year which allowed a one tap Jailbreak and a fast unlock for users. Apple had fixed the flaw in its early stages and now its back. Looks like that is the reason for the quick iPad 2 Jailbreak and the new exploit the Jailbreakers have been enjoying. According to the Wall Street Journal, Apple acknowledged the exploit, and is working on an update. The said update will not only fix the JailbreakMe 3.0 exploit but also another exploit that could allow unwanted eyes to your information.
[dropcap]T[/dropcap]he PDF exploit that was used in JailreakMe last year which allowed a one tap Jailbreak and a fast unlock for users. Apple had fixed the flaw in its early stages and now its back. Looks like that is the reason for the quick iPad 2 Jailbreak and the new exploit the Jailbreakers have been enjoying. According to the Wall Street Journal, Apple acknowledged the exploit, and is working on an update. The said update will not only fix the JailbreakMe 3.0 exploit but also another exploit that could allow unwanted eyes to your information. -
Al-Qaida Communications Offline
Terrorist group Al-Qaida has been left without a distribution channel on the Internet, says terrorism expert Evan Kohlmann of Flashpoint Partners. In an e-mail he sent on Wednesday, he said
[quote]I really can’t say for certain how or why this happened, other than that it involved apparently separate attacks on both the domain name and data server used by al-Qaida’s trusted forum, Al-Shamukh. That kind of coordinated event doesn’t typically occur by happenstance.[/quote]
Kohlmann, who has spent a decade tracking Al-Qaida, has said that other jihadi forums have been left online for the “rabble” to communicate. However, none of these forums are trusted by members of Al-Qaida. The incident, which started around 72 hours ago, began with the hijacking of the primary web domain used by the Shamukh chat forum, which disseminates propaganda on behalf of Al-Qaida. The next phase of the attack involved crippling the Shamukh website along with two other top level jihadi forums, including the Arabic-language Ansar al-Mujahideen Network.
He said that Al-Qaida most certainly had a backup of the Shamukh forum database, but there are no other channels left for the terrorist organisation to distribute new material. Either the forum must be brought back online, or they must establish a new relationship with another forum.
A list of potential suspects who brought down the Al-Qaida site includes government sponsored hackers from the US and the UK as well as independent cyber vigilantes.
-

George Hotz (Geohot) joins Facebook as product developer
 Internet’s more well-known celebrity iPhone and PlayStation hacker George “GeoHot” Hotz has gone to Facebook. Rumors say that he’s involved with product development for the company’s alleged iPad app. The news was confirmed by a quick visit to Hotz’s Facebook page, his work status shows “Facebook software engineer starting in May 2011”
Internet’s more well-known celebrity iPhone and PlayStation hacker George “GeoHot” Hotz has gone to Facebook. Rumors say that he’s involved with product development for the company’s alleged iPad app. The news was confirmed by a quick visit to Hotz’s Facebook page, his work status shows “Facebook software engineer starting in May 2011”Hotz himself is responsible for the outbreak of the Internet unlocking community due to his successful manipulations of both Apple iPhones and iPod Touches as well as Sony’s PlayStation 3. The latter caused a four-month legal battle between Sony and Hotz. The hacktivist group Anonymous launched a distributed denial of service attack against Sony in April to retaliate for the company going after Hotz.
-

Governments vs Hackers – Cyberwar Continues #AntiSec
The AntiSec Campaign which started a few days ago as a partnership between hacker groups LulzSec and Anonymous, is a cat and mouse game between the hackers and the governments they target. One member of LulzSec, Ryan Cleary, a 19 year old from Wickford, Essex, UK, is suspected by authorities to be a leader of the group as well as being the brains behind the attacks on the FBI, CIA and Sony sites. He was arrested by British Police yesterday in a “pre-planned intelligence raid”. He has allegedly performed these acts from a computer in his mother’s house.
In another part of the world, the Brazilian wing of LulzSec seems to be accomplishing their mission(s) quite well. In a tweet from Lulzsec, the group congratulated their Brazilian unit.
[quote]Our Brazilian unit is making progress. Well done @LulzSecBrazil, brothers![/quote]
Meanwhile, Anonymous has not been sitting idle. In a video released a few hours ago, the group urged anyone from around the world who believed in freedom of speech and anti-censorship of the Internet to stand up for their rights and join them.
This cyber war seems to be heating up, with the hackers targeting governments around the world. We shall keep you updated on the action as it happens. Stay tuned.
-

Anonymous and LulzSec Announce New Campaign
The two most famous hacker groups in recent times have united in a campaign which they call AntiSec. The targets include banks, government organizations, and other high profile targets. They are urging hackers from around the world to unite to steal and leak classified documents, e-mails, and other information. [quote]We hear our #Anonymous brothers are making progress with #AntiSec, we also have reports of many rogue hacker groups joining in. :D[/quote] the group tweeted a few hours ago.
The campaign seems to have hit its first official target target today. The website of UK based Serious Organised Crime Agency was down today. In another tweet, it appears pastebin, the text sharing site appears to be down. LulzSec suspects the UK Government to have perpetrated an attack against the site as the group uses it to distribute materials. They tweeted:[quote]#DearGovernment did you DDoS @Pastebin b/c of this pastebin.com/9KyA0E5v #AntiSec or is that b/c of us reading it?[/quote] When we visited the website, this is what we found:
LulzSec is a group that recently targeted the CIA, the FBI, and Sony among others. The group seems to want to embarrass their targets just for kicks and are speculated to be an offshoot of Anonymous.
Anonymous is a group that targets governments and organizations for political reasons and mostly in the support of freedom of speech. In the past they have targeted the governments of Iran, Turkey and Egypt. They have also targeted Sony for the company’s legal action against PlayStation 3 hacker George Hotz, and Paypal, MasterCard and VISA after they removed their services from the WikiLeaks website which enabled the site to receive donations.
Stay tuned for more news on the on-going cyber war.
-

LulzSec Reveals Motives Behind its Hacks (PR)
 LulzSec has been on a hacking rampage for a while now. On reaching a 1000 tweet milestone, they have decided to reveal their motives to friends and foes alike in a Press Release they posted on PasteBin.
LulzSec has been on a hacking rampage for a while now. On reaching a 1000 tweet milestone, they have decided to reveal their motives to friends and foes alike in a Press Release they posted on PasteBin.[toggle title_open=”Collapse Press Release” title_closed=”Expand Press Release” hide=”yes” border=”yes” style=”default” excerpt_length=”0″ read_more_text=”Read More” read_less_text=”Read Less” include_excerpt_html=”no”]Dear Internets,
This is Lulz Security, better known as those evil bastards from twitter. We just hit 1000 tweets, and as such we thought it best to have a little chit-chat with our friends (and foes).
For the past month and a bit, we’ve been causing mayhem and chaos throughout the Internet, attacking several targets including PBS, Sony, Fox, porn websites, FBI, CIA, the U.S. government, Sony some more, online gaming servers (by request of callers, not by our own choice), Sony again, and of course our good friend Sony.
While we’ve gained many, many supporters, we do have a mass of enemies, albeit mainly gamers. The main anti-LulzSec argument suggests that we’re going to bring down more Internet laws by continuing our public shenanigans, and that our actions are causing clowns with pens to write new rules for you. But what if we just hadn’t released anything? What if we were silent? That would mean we would be secretly inside FBI affiliates right now, inside PBS, inside Sony… watching… abusing…
Do you think every hacker announces everything they’ve hacked? We certainly haven’t, and we’re damn sure others are playing the silent game. Do you feel safe with your Facebook accounts, your Google Mail accounts, your Skype accounts? What makes you think a hacker isn’t silently sitting inside all of these right now, sniping out individual people, or perhaps selling them off? You are a peon to these people. A toy. A string of characters with a value.
This is what you should be fearful of, not us releasing things publicly, but the fact that someone hasn’t released something publicly. We’re sitting on 200,000 Brink users right now that we never gave out. It might make you feel safe knowing we told you, so that Brink users may change their passwords. What if we hadn’t told you? No one would be aware of this theft, and we’d have a fresh 200,000 peons to abuse, completely unaware of a breach.
Yes, yes, there’s always the argument that releasing everything in full is just as evil, what with accounts being stolen and abused, but welcome to 2011. This is the lulz lizard era, where we do things just because we find it entertaining. Watching someone’s Facebook picture turn into a penis and seeing their sister’s shocked response is priceless. Receiving angry emails from the man you just sent 10 dildos to because he can’t secure his Amazon password is priceless. You find it funny to watch havoc unfold, and we find it funny to cause it. We release personal data so that equally evil people can entertain us with what they do with it.
Most of you reading this love the idea of wrecking someone else’s online experience anonymously. It’s appealing and unique, there are no two account hijackings that are the same, no two suddenly enraged girlfriends with the same expression when you admit to killing prostitutes from her boyfriend’s recently stolen MSN account, and there’s certainly no limit to the lulz lizardry that we all partake in on some level.
And that’s all there is to it, that’s what appeals to our Internet generation. We’re attracted to fast-changing scenarios, we can’t stand repetitiveness, and we want our shot of entertainment or we just go and browse something else, like an unimpressed zombie. Nyan-nyan-nyan-nyan-nyan-nyan-nyan-nyan, anyway…
Nobody is truly causing the Internet to slip one way or the other, it’s an inevitable outcome for us humans. We find, we nom nom nom, we move onto something else that’s yummier. We’ve been entertaining you 1000 times with 140 characters or less, and we’ll continue creating things that are exciting and new until we’re brought to justice, which we might well be. But you know, we just don’t give a living fuck at this point – you’ll forget about us in 3 months’ time when there’s a new scandal to gawk at, or a new shiny thing to click on via your 2D light-filled rectangle. People who can make things work better within this rectangle have power over others; the whitehats who charge $10,000 for something we could teach you how to do over the course of a weekend, providing you aren’t mentally disabled.
This is the Internet, where we screw each other over for a jolt of satisfaction. There are peons and lulz lizards; trolls and victims. There’s losers that post shit they think matters, and other losers telling them their shit does not matter. In this situation, we are both of these parties, because we’re fully aware that every single person that reached this final sentence just wasted a few moments of their time.
Thank you, bitches.
Lulz Security[/toggle]
The press release states that they have been causing mayhem and chaos throughout the Internet, attacking several targets including PBS, Sony, Fox, porn websites, FBI, CIA, the U.S. government and online gaming servers. In their defence they claim that they have publically announced their hacks (not all of them), and that other hacker groups have not been so forthcoming. It appears that they will continue on their hacking rampage until they are brought to justice.
-
Sony Ericsson’s Canadian Online store Hacked, Sony in the Crosshair

Sony has been targeted by Hackers yet again. In the biggest attack against an organization, hackers all over the world are taking revenge for their rights with Sony. After several attacks including PSN, SONY BMG, and even a service all owned by Sony, This time its Sony Ericsson’s Canadian Online store and the intrusion extracted personal data of more than 2,000 Canadian Eshop customers.
According to SE the passwords taken were encrypted and no credit card details were lost. Hopefully SONY will tighten its security post these attack making it one of the most secure Company with online presence.
On Tuesday, security firm Sophos said Sony Music Japan suffered the same fate — with hackers exploiting a system vulnerability and posting such taunts as “stupid Sony, so very stupid” inside the data they made available online.
And while the series of attacks suggest Sony has more work to do securing its networks Phil Lieberman, CEO of online security consulting firm Lieberman Software, said it is also the price Sony is paying for its hard-line approach to the hacking community.
[BBC]
-

Sony’s Security continues to fail, Subsidiary So-Net Entertainment attacked
 According to The Wall Street Journal hackers have accessed the customer accounts of Sony subsidiary So-net Entertainment Corp, an ISP, and have stolen about $1,225 worth of redeemable gift points. This after the massive breach of Sony’s Playstation Network which caused a loss of 12.3 million credit card numbers from the networks database.
According to The Wall Street Journal hackers have accessed the customer accounts of Sony subsidiary So-net Entertainment Corp, an ISP, and have stolen about $1,225 worth of redeemable gift points. This after the massive breach of Sony’s Playstation Network which caused a loss of 12.3 million credit card numbers from the networks database.Sony said the So-net hacker tried to break into its systems more than 10,000 times before he or she was able to successfully log-in. The intruder was able to access 201 accounts, and he or she stole the redeemable points from 128 customers.
“Although we can’t completely rule out the possibility that there is a connection with the PSN issue, the likelihood is low,” said So-net Entertainment spokesperson Keisuke Watabe, noting that the style of attack was different.


