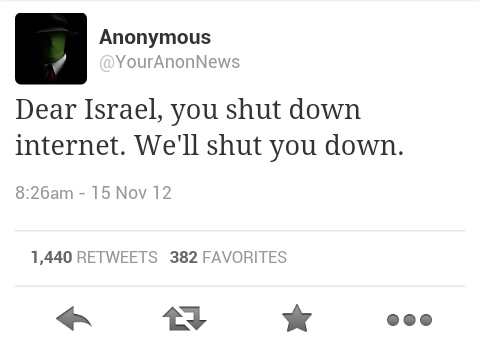
 LulzSec has been on a hacking rampage for a while now. On reaching a 1000 tweet milestone, they have decided to reveal their motives to friends and foes alike in a Press Release they posted on PasteBin.
LulzSec has been on a hacking rampage for a while now. On reaching a 1000 tweet milestone, they have decided to reveal their motives to friends and foes alike in a Press Release they posted on PasteBin.
[toggle title_open=”Collapse Press Release” title_closed=”Expand Press Release” hide=”yes” border=”yes” style=”default” excerpt_length=”0″ read_more_text=”Read More” read_less_text=”Read Less” include_excerpt_html=”no”]Dear Internets,
This is Lulz Security, better known as those evil bastards from twitter. We just hit 1000 tweets, and as such we thought it best to have a little chit-chat with our friends (and foes).
For the past month and a bit, we’ve been causing mayhem and chaos throughout the Internet, attacking several targets including PBS, Sony, Fox, porn websites, FBI, CIA, the U.S. government, Sony some more, online gaming servers (by request of callers, not by our own choice), Sony again, and of course our good friend Sony.
While we’ve gained many, many supporters, we do have a mass of enemies, albeit mainly gamers. The main anti-LulzSec argument suggests that we’re going to bring down more Internet laws by continuing our public shenanigans, and that our actions are causing clowns with pens to write new rules for you. But what if we just hadn’t released anything? What if we were silent? That would mean we would be secretly inside FBI affiliates right now, inside PBS, inside Sony… watching… abusing…
Do you think every hacker announces everything they’ve hacked? We certainly haven’t, and we’re damn sure others are playing the silent game. Do you feel safe with your Facebook accounts, your Google Mail accounts, your Skype accounts? What makes you think a hacker isn’t silently sitting inside all of these right now, sniping out individual people, or perhaps selling them off? You are a peon to these people. A toy. A string of characters with a value.
This is what you should be fearful of, not us releasing things publicly, but the fact that someone hasn’t released something publicly. We’re sitting on 200,000 Brink users right now that we never gave out. It might make you feel safe knowing we told you, so that Brink users may change their passwords. What if we hadn’t told you? No one would be aware of this theft, and we’d have a fresh 200,000 peons to abuse, completely unaware of a breach.
Yes, yes, there’s always the argument that releasing everything in full is just as evil, what with accounts being stolen and abused, but welcome to 2011. This is the lulz lizard era, where we do things just because we find it entertaining. Watching someone’s Facebook picture turn into a penis and seeing their sister’s shocked response is priceless. Receiving angry emails from the man you just sent 10 dildos to because he can’t secure his Amazon password is priceless. You find it funny to watch havoc unfold, and we find it funny to cause it. We release personal data so that equally evil people can entertain us with what they do with it.
Most of you reading this love the idea of wrecking someone else’s online experience anonymously. It’s appealing and unique, there are no two account hijackings that are the same, no two suddenly enraged girlfriends with the same expression when you admit to killing prostitutes from her boyfriend’s recently stolen MSN account, and there’s certainly no limit to the lulz lizardry that we all partake in on some level.
And that’s all there is to it, that’s what appeals to our Internet generation. We’re attracted to fast-changing scenarios, we can’t stand repetitiveness, and we want our shot of entertainment or we just go and browse something else, like an unimpressed zombie. Nyan-nyan-nyan-nyan-nyan-nyan-nyan-nyan, anyway…
Nobody is truly causing the Internet to slip one way or the other, it’s an inevitable outcome for us humans. We find, we nom nom nom, we move onto something else that’s yummier. We’ve been entertaining you 1000 times with 140 characters or less, and we’ll continue creating things that are exciting and new until we’re brought to justice, which we might well be. But you know, we just don’t give a living fuck at this point – you’ll forget about us in 3 months’ time when there’s a new scandal to gawk at, or a new shiny thing to click on via your 2D light-filled rectangle. People who can make things work better within this rectangle have power over others; the whitehats who charge $10,000 for something we could teach you how to do over the course of a weekend, providing you aren’t mentally disabled.
This is the Internet, where we screw each other over for a jolt of satisfaction. There are peons and lulz lizards; trolls and victims. There’s losers that post shit they think matters, and other losers telling them their shit does not matter. In this situation, we are both of these parties, because we’re fully aware that every single person that reached this final sentence just wasted a few moments of their time.
Thank you, bitches.
Lulz Security[/toggle]
The press release states that they have been causing mayhem and chaos throughout the Internet, attacking several targets including PBS, Sony, Fox, porn websites, FBI, CIA, the U.S. government and online gaming servers. In their defence they claim that they have publically announced their hacks (not all of them), and that other hacker groups have not been so forthcoming. It appears that they will continue on their hacking rampage until they are brought to justice.
 Microsoft said that it had eyes on a similar set of websites since 2013, which were being operated by hackers for negative intent. The company has previously tried to snoop on defence industry workers, political activists and journalists in the Middle East. Microsoft tied the attacks to the country of Iran, not to its Government. Furthermore, Iran has fully denied any participation in hacking attacks made by the aforementioned hackers.
Microsoft said that it had eyes on a similar set of websites since 2013, which were being operated by hackers for negative intent. The company has previously tried to snoop on defence industry workers, political activists and journalists in the Middle East. Microsoft tied the attacks to the country of Iran, not to its Government. Furthermore, Iran has fully denied any participation in hacking attacks made by the aforementioned hackers. Noteworthy, the accounts that were being targeted by the users were personal accounts, not work based accounts. The hackers used to send surprisingly legitimate-looking emails with malware-infected attachments to users who would then click on them and have the respective software injected on their devices. The domains used by the hackers closely resembled the ones used by Microsoft and other reputed brands.
Noteworthy, the accounts that were being targeted by the users were personal accounts, not work based accounts. The hackers used to send surprisingly legitimate-looking emails with malware-infected attachments to users who would then click on them and have the respective software injected on their devices. The domains used by the hackers closely resembled the ones used by Microsoft and other reputed brands. Also Read: Xiaomi’s Foldable Smartphone Spotted In Official Video Promo
Also Read: Xiaomi’s Foldable Smartphone Spotted In Official Video Promo











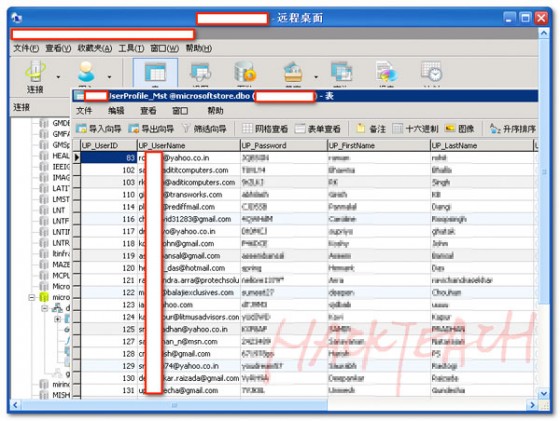






 In a recent cyber attack by
In a recent cyber attack by 