Windows 10 Plagued With Zero-Day Vulnerability With May Update

Microsoft released its latest Windows 10 update that boasts of numerous improvements. However, the changes bring about a new form of security threat for the freshly updated Microsoft Windows 10 operating system. Since Microsoft had announced the aforementioned update on May 21st, it is safe to assume that the update would still need a couple of days to be more widespread.
 The update brings new things to the table such as Windows Sandbox and refreshes the Start menu to be simpler on newer devices. Microsoft with this updated software brings a change in the manner Windows 10 handles reserved storage. Furthermore, Cortana has now been moved from the search tab as well.
The update brings new things to the table such as Windows Sandbox and refreshes the Start menu to be simpler on newer devices. Microsoft with this updated software brings a change in the manner Windows 10 handles reserved storage. Furthermore, Cortana has now been moved from the search tab as well.
Microsoft has been known to have a passive approach to the release of their software updates, hence most users would not be receiving the said update immediately. To check if the update is available clicking on the Windows Update option under Update and Security can be found in the System’s Settings.

Zero-Day vulnerability or 0-Day vulnerability, for those not aware of technical jargons, is a computer vulnerability that has not been discovered by the vendor or main party in concern (here Microsoft). The classification remains until the main party acknowledges the issue that can be abused by exploiters/hackers.
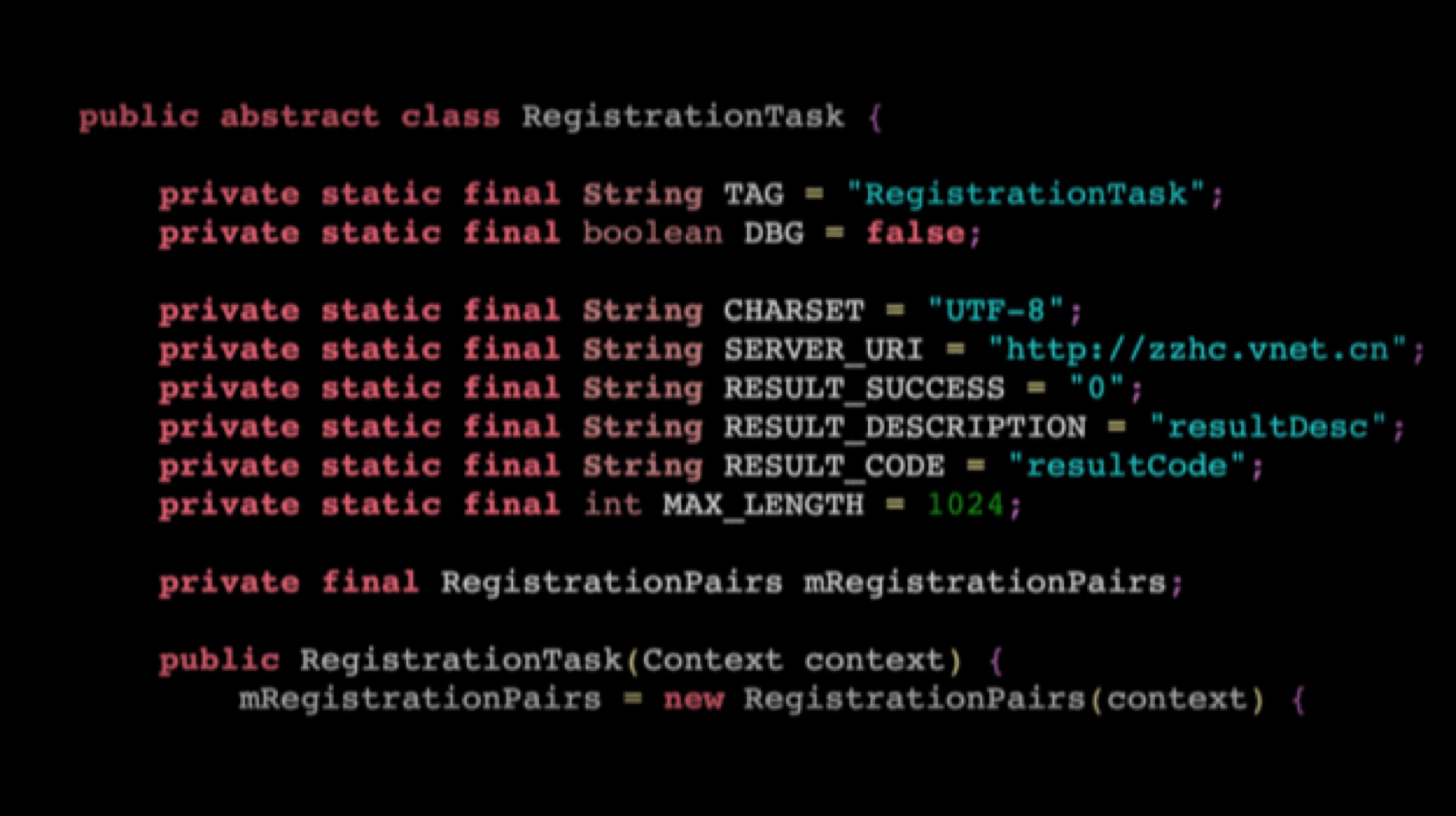
A researcher named SandboxEscaper published the exploit code on GitHub and released a video of how the exploit can be abused. SandboxEscaper has been known to have discovered other such zero-day exploits. The vulnerability in question targets the local privilege escalation (LPE) that allows third-party complete access to the machine by granting them administrator status over the actual user. In other words, a users computer may be remotely accessed by those who seek to gain access.
Also Read: Xiaomi Black Shark 2 To Be Retailed Via Flipkart In India, Launching On 27 May
The zero-day cannot be exploited in and of itself but paves the way for other methods to have more of an effect when used simultaneously. SandboxEscaper reports that the Windows Task Scheduler is the vulnerability that makes the exploit possible. If the hacker used a particular .job file in the Windows Task Scheduler after gaining access to the computer, it grants administrator access to the system giving the hacker unwarranted power to change fundamental settings on the PC.